A cursory glance at just the last two years alone shows an alarming, ever-rising trend of data breaches. From small practices to healthcare giants, it seems no one is safe from data breach losses - money, time and patient trust.
Worse yet, it’s not just the big names that are falling victim to bad guys. “In small office and home office networks, the data is every bit as important as the data in the larger networks,”1 states David Reed in a SANS Institute white paper.
But there’s some good news. There’s one precaution that every organization, big and small, can take against the threat of costly data breaches: whole disk encryption. If you haven’t been protecting your data already, here are the top three reasons why you should start right away.
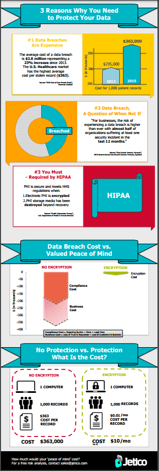
#1 You Can’t Afford Not To
The cost of a data breach is usually expressed in terms of cost per record. These figures aren’t just an estimate of fines; they also include other costs that typically result from damage control after a data breach:
• Investigation and remediation of security flaws
• Notification via mail to those customers whose data was compromised
• Identity theft protection for all victims
• Opportunity cost of spending more time on fixing the breach and less time on usual business activities
• Lawsuits from disgruntled victims
The Ponemon Institute estimates that the “average global cost of data breach per lost or stolen record is $154.” From there, actual cost per record can vary depending on the industry. For instance, according to Ponemon’s research, the U.S. Healthcare market has the highest average cost per stolen record: “if a healthcare organization has a breach, the average cost could be as high as $363, and in education the average cost could be as high as $300.”2
Practically speaking, when just one lost computer holds 1000 health records, a data breach could cost you up to $363,000!
#2 When Not If
Much like car accidents or house fires, a data breach seems to be one of those things that you think will never happen to you… until it does. In its 2015 Data Breach Industry Forecast, Experian explains that, “for businesses, the risk of experiencing a data breach is higher than ever with almost half of organizations suffering at least one security incident in the last 12 months.”3
And small businesses are far from immune from these threats. The risk of a data breach is so high, in fact, that the FBI has sternly warned businesses everywhere to prepare for the worst. “You’re going to be hacked,” Joseph Demarest, assistant director of the FBI’s cyber division, famously cautioned in late 2014. “Have a plan.”4
#3 It’s The Law
While jurisdictions across the United States continue to experiment with data breach laws, the Healthcare industry is already mandated to comply with certain data protection and breach notification standards by the Health Insurance Portability and Accountability Act (HIPAA).
According to the U.S. Department of Health and Human Services (HHS)5, Protected Health Information (PHI) is secure when:
• Electronic PHI is encrypted
• PHI storage media has been destroyed beyond recovery
As data protection becomes increasingly important to the public, HIPAA is continually reviewed for effectiveness and covered entities more routinely audited for compliance. To ensure that PHI records are sufficiently protected, the Office for Civil Rights (OCR) has already dedicated a budget of $43 million for compliance audits in 2016, an increase of $4 million over the 2015 budget of $39 million.
And Now, The Good News
Cybersecurity experts around the world agree that regular use of disk encryption software should be a key component of any organization’s data breach preparedness plan.
Crisis management plans for data breaches usually focus on what to do after a breach; for instance, notifying stakeholders and investigating the vulnerabilities that led to the attack. But prevention, of course, is the best medicine - and the best prevention is whole disk encryption. As David Reed of the SANS Institute concludes, “Using encryption on each device that has the ability is among the best ways to prevent unauthorized access to data.”
Even if you think your organization is too new, too small or too busy to implement a full crisis management plan, encrypting your data is a simple, proactive measure that you can take right now. With a relatively small amount of money for an encryption solution, organizations can significantly reduce the cost of a data breach down the road. And perhaps just as important, they can protect their reputation as a responsible steward of customer data.
HIPAA Compliant Encryption Software By Jetico
Jetico provides pure and simple data encryption software for National Security, Compliance and Personal Privacy. To protect stored data, Jetico's BestCrypt delivers HIPAA compliant encryption software for whole disks, virtual drives and selected files or folders. Jetico Enterprise Editions include central management for client software control.

Need A Quick Recap?
Click here for an illustrated summary of why you need data encryption.
Free Risk Analysis
How much would your peace of mind cost? Click here to obtain a free risk analysis.
1 Reed, David. “Encryption Solutions for Small Networks.” SANS Institute white paper, November 13, 2015. [Online], Available: www.giac.org/paper/gsec/37592/encryption-solutions-small-networks/147882 [06 Apr 2016]
2 IBM. “Ponemon Institute’s 2015 Global Cost of Data Breach Study Reveals Average Cost of Data Breach Reaches Record Levels.” IBM press release, May 27, 2015. [Online], Available: www-03.ibm.com/press/us/en/pressrelease/47022.wss [06 Apr 2016]
3 Experian. “2015 Second Annual Data Breach Industry Forecast.” Experian white paper. [Online], Available: www.experian.com/assets/data-breach/white-papers/2015-industry-forecast-experian.pdf [06 Apr 2016]
4 Kelly, Erin. “Officials warn 500 million financial records hacked.” USA Today, October 20, 2014. [Online], Available: www.usatoday.com/story/news/politics/2014/10/20/secret-service-fbi-hack-cybersecuurity/17615029/ [06 Apr 2016]
5 U.S. Department of Health & Human Services. "Guidance to Render Unsecured Protected Health Information Unusable, Unreadable, or Indecipherable to Unauthorized Individuals." [Online], Available: www.hhs.gov/ocr/privacy/hipaa/administrative/breachnotificationrule/brguidance.html [06 Apr 2016]